Sometimes there are just too many connections in your network and your FMC cannot handle them. Especially virtual FMC is not very good syslog collector (there is limit of connection in DB). FMC is more suitable as a SIEM – all your security events should still be sent to FMC.
Cisco FTD eventing design
When you want to log all the connection information there will be lots of syslogs, and you should have more robust logging and storage infrastructure. In this article we will focus on more robust eventing (syslog) infrastructure from the point of firewalls (Cisco FMC + FTD). Description of syslog server infrastructure/collectors/processors is not part of this article.
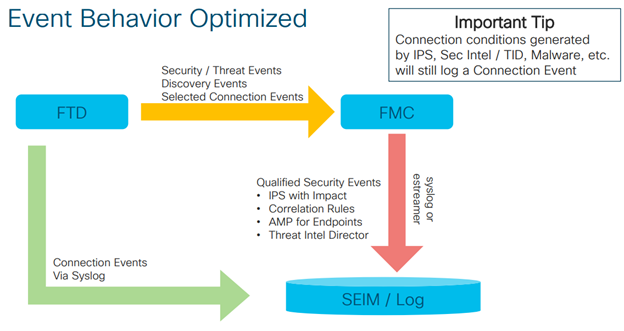
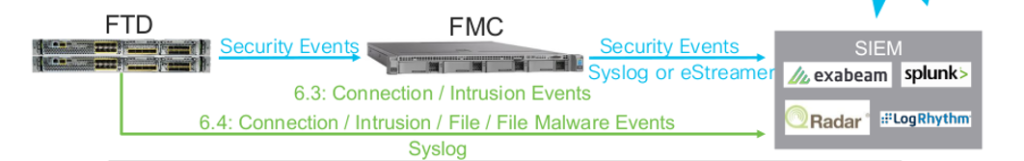
When there are many events to log, Cisco recommends to use separate eventing infrastructure. You can dedicate one physical interface for syslogs = eventing traffic on your firewall chassis. Therefore, eventing traffic will not interfere with your management traffic on MGMT0 interface. Check the high level description of event flows:
FTD firewall will send syslogs to the SIEM without spamming eventing database of the FMC. However, all the important security events will be still delivered to the FMC. If you want, you can select some connections to be still logged in the FMC connection event table.
Configuration
I am attaching a couple of screenshots from my virtual FMC deployment – version 6.6.1. Firewalls are Firepower 4125. I will not go deep into the settings – most of them are self-explanatory. Please refer to FMC configuration guide for more details.
Configuration is divided to 3 parts:
- Interface and IP settings
- Device platform policy
- Access control policy
Interface and IP settings
Dedicate one physical interface in the Firepower Device Manager. 1Gbps should be enough.
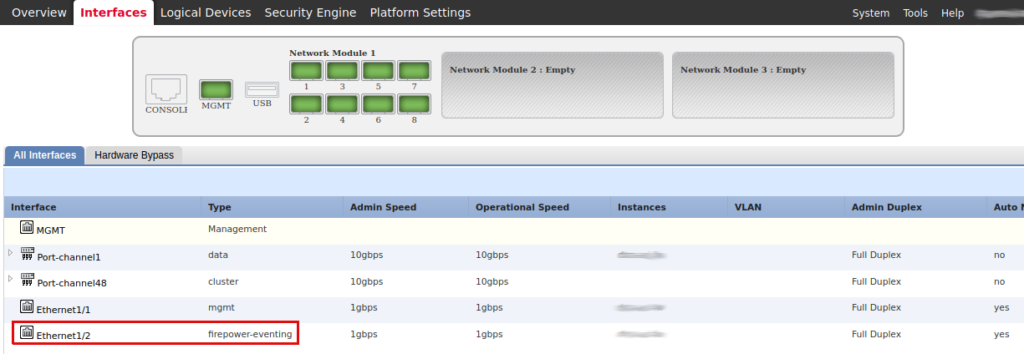
Dedicate one interface for event traffic in the FMC (Configuration -> Management Interfaces).
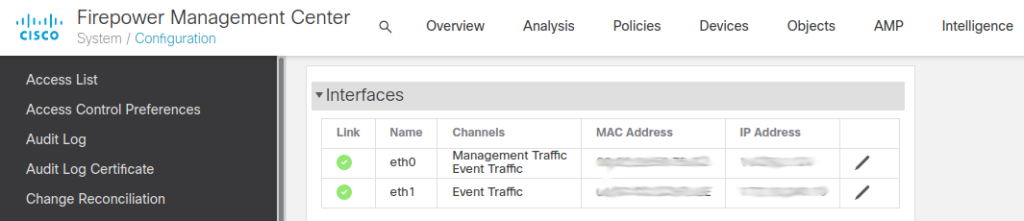
In the FMC you can set the IP address of the eventing interface. I haven’t found how to configure FTD eventing interface using GUI. I used the following commands in FXOS CLI. Check the FTD command reference for more information.
If you configure an event-only interface, then you must enter the gateway_ip as part of the command; however, this entry just configures the default route to the value you specify and does not create a separate static route for the eventing interface. If you are using an event-only interface on a different network from the management interface, Cisco recommends that you set the gateway_ip for use with the management interface, and then create a static route separately for the event-only interface.
# login to fxos! Not ftd directly
# then: connect module 1 console, connect ftd
# (don’t use ssh as it will disconnect you while setting IP)
# enable interface and event channels
configure network management-interface enable management1
configure network management-interface disable-event-channel management0
configure network management-interface enable-event-channel management1
configure network management-interface enable-management-channel management1# check network settings
show network# change the IP of the new interface. WARNING: this will also change the default gateway of the mgmt0
configure network ipv4 manual 172.16.1.100 255.255.255.0 172.16.1.254 management1
# enter the same IP address for management0 as there was before – last command changed default gateway. You have to configure it back. I haven’t found a better way – that’s why you should connect to consol from fxos
configure network ipv4 manual 172.16.0.100 255.255.255.0 172.16.0.254 management0# check network settings again after change and try to ping something
show network
ping system 172.18.19.20
# edit static routes for eventing interface if needed
configure network static-routes ipv4 add management1 10.1.1.0 255.255.255.0 172.16.1.254
show network-static-routes
Device platform policy
All the syslog related settings can be tuned here : Device > Platform Settings > Syslog. Also, you have to alter Access Control Policy settings – we will cover it at the end.
- First enable logging and alter logging settings:
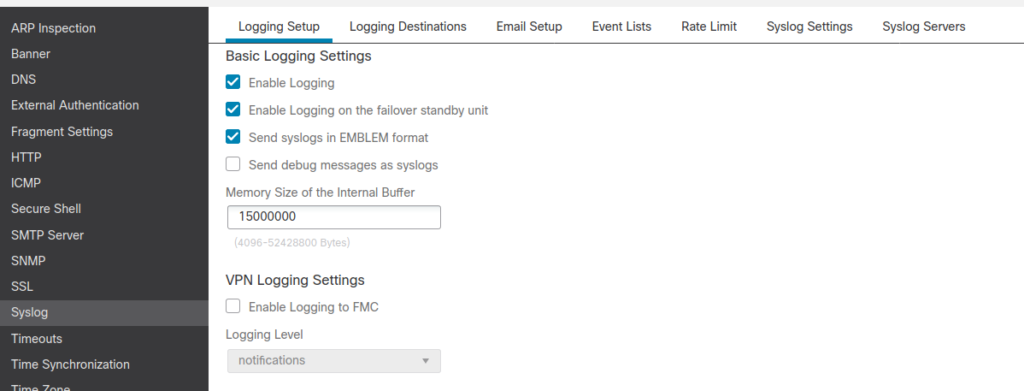
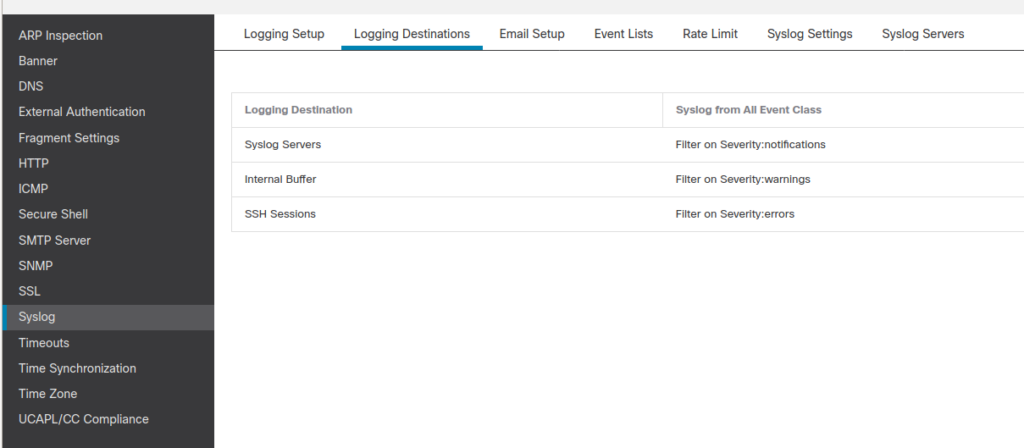
2. Specify which syslogs should be sent to which destinations. We don’t specify the IP address of the syslog yet. Just specify the severity or particular syslog IDs to be sent. I usually have different settings for logging to syslog servers, logging to internal firewall buffer and logging to monitor of ssh sessions.
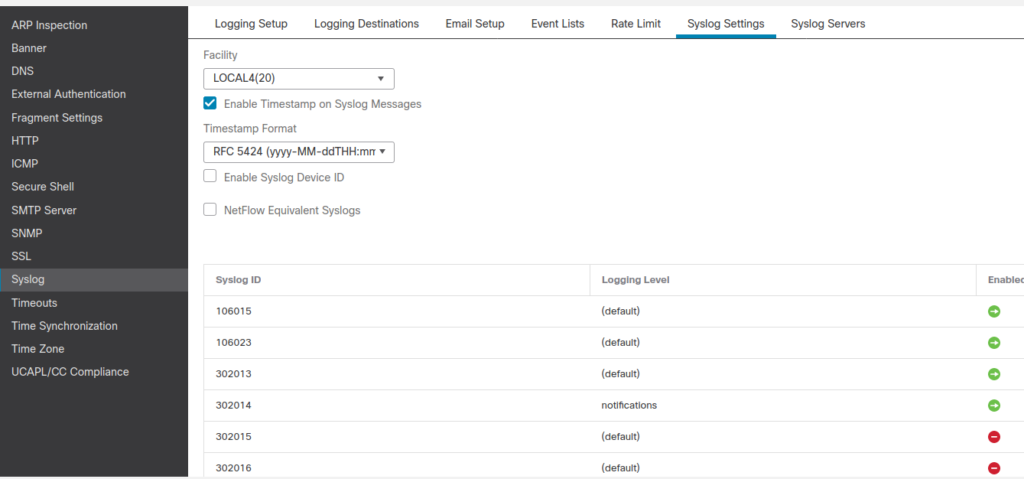
3. I skipped a couple of tabs in the top menu, but go and check them out. In the tab “Syslog settings” you can specify the format of the syslogs. By default, sending of all the NetFlow equivalent Syslogs is disabled (checkbox shown below is checked). I unchecked this option so that I can receive more information about connection creations/terminations. You could see those syslogs in the ASA logging.
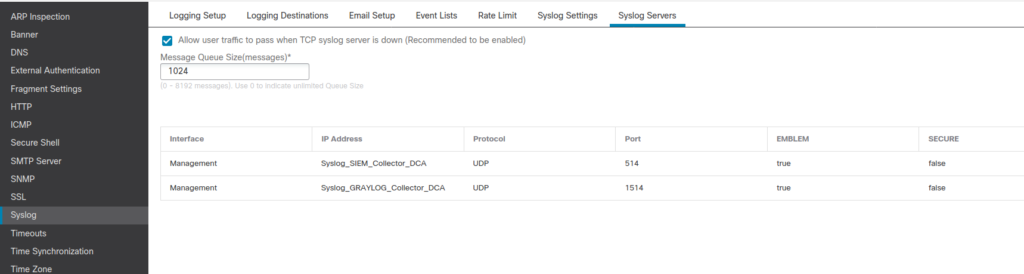
4. The Last thing to do in the device platform settings is to specify information about syslog receivers / servers. Mainly IP address and the port on which server is listening for syslogs.
Access control policy
Since FTD 6.3 syslogs can be sent from FTD directly. Configure general syslog settings for every Access control policy.
Configure logging in your access control policies to inherit the logging settings from the platform settings policy. (Under Policies > Access Control Policy >Logging check the FTD 6.3 and later: Use the syslog settings configured in the FTD Platform Settings)
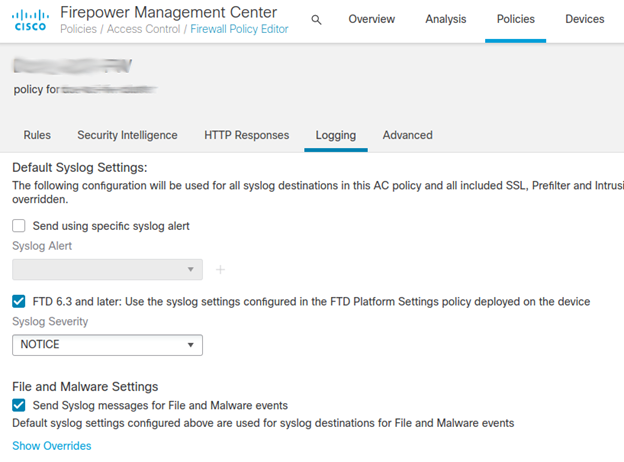
With these two configuration settings in place the FTD syslog settings in the platform settings policy apply to:
- syslog messages related to device and system health, and network configuration.
- syslogs for connection and security intelligence events
- syslogs for intrusion events
Then, you have to specify logging preferences for every rule. Specify if the event about connection handled by this rule should be sent to SIEM or to FMC also. I recommend sending events only at the end of the connection – you will receive more details gathered at the connection teardown.
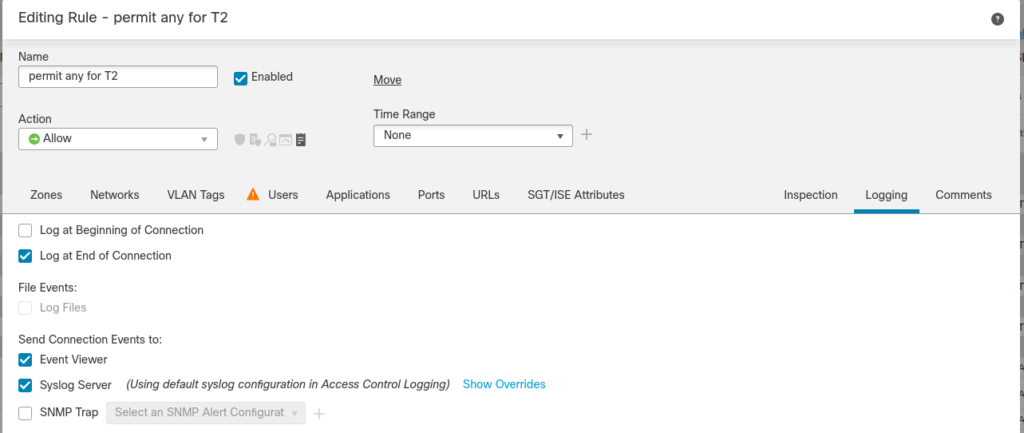
Example of syslog message
With newer FTDs you will receive new types of Syslog events. You can find all relevant information in one syslog event. I recommend you to make parsers for these new syslog IDs 430001 – 430005. Check detailed information in Cisco documentation.

This is an example of syslog event 430003. You can find many FMC and flow related information in the body.
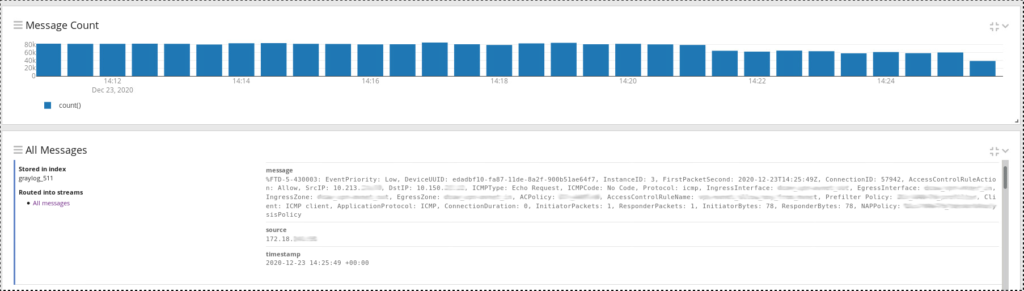
Happy parsing ! :)